Engineering & Technology
Security And Privacy Issues Over The Cloud Environment: Tips For Developing Secure Cloud Model 2019
Sep 17, 2019RESEARCH REPORT
In Brief:
General background
Over the past decades, there is a rapid growth of data generated in the form of unstructured, semi-structured and unstructured [1] which is from multiple resources. For instances, various organization, government sector, social network website and medical applications that serve around millions of web page views per day, but the storage and maintenance of these huge data becomes complex and cannot be handled by traditional data management systems [2]. Hence there is a need of new frameworks, platforms and novel techniques for data safety, data management, privacy maintenance, and data analytics [3]. Among these, there is a special focus required for privacy and security of our data [4] [5] [6]. Apart from the security and privacy issue, the following questions are significant issues:
“How to make good use of data,
How to maintain the user privacy,
How to guarantee data availability
While ensuring the data security”
See also: Secure Access Control Framework for Fully Fledged Network Security Control
See also: Tips for developing secure and flexible management policy
Security and privacy concern
From an academic and industrial point of view, the encryption process will be an effective solution toward solving the privacy and security issues. Also, it protects the sensitive information which is outsourced as long as the data has been encrypted through data owner before upload to the trusted cloud system. But, till date, there is a lack of effective approach to offering secure access on cloud services and complex due to the open nature of the wireless communication medium (Sundareswaran et al., 2012; Peng et al., 2012; Qin et al., 2016; Jegadeesan et al., 2019).
The primary security requirements includes data transparency, availability, authentication, integrity confidentiality, and audits as specified [10]. Similarly, the privacy requirements are like malicious insiders, insecure APIs, shared technology issues, account hijacking and so on [11].
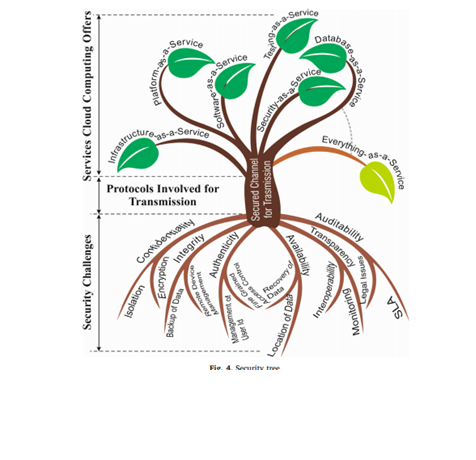
cloud environment [10]
There is a need of following recommendations:
- Secure access control framework for full-fledged network security control.
- Flexible management policy which should considering a large number of users.
- Effective machine learning technique to handle cloud resources and load balancing task for both private and public cloud.
- Effective scheduling technique to handle multiple workflow with considering multiple priorities at different times in cloud.
- Suitable machine learning technique to find and differentiating pattern of data from multiple sources.
- Solve and optimize the security and decision-making issues via artificial intelligence.
- Implement effective Soft computing technique to detect network attacks where we can solve the hacking issues.
- Implement the effective web mining technique to discover the knowledge in web-based environments.
Summary
Till date, there is a lack of effective approach to offering secure access cloud model and services. This is due to the open nature of the data from multiple sources. Hence I have suggested the above recommendations for full-fledged network secure model. It can be concluded that the different kinds of management system, the Cloud service providers (CSPs) have more responsibility in cloud environment. Also, the sensitive data requires security and privacy concern from both cloud users and CSPs.


