Engineering & Technology
Secure Access Control Framework For Fully Fledged Network Security Control: How Machine Learning Algorithms Helps To Improve Security.
Sep 17, 2019RESEARCH REPORT
In Brief:
- AI promises to booth data access control in cloud computing platforms.
- Developing a novel algorithm using the ML approach to classify user’s behaviour is significant to bridge the gap among theory and real-time application.
- The access control and security management framework along with effective ML would provide guidance information for the cloud customers and administrators to make decisions.
The access control and security management framework along with effective machine learning would provide guidance information for the cloud customers and administrators to make decisions, for instance, migrating tasks from dynamically allocating resources, suspect nodes to trustworthy nodes and managing the trade-off among the cost of resources and degree of redundancy.At the present scenario, the cloud environment widely used in numerous fields, namely, web applications, healthcare, mobile social networks, e-commerce, data storage, gaming, and so on. Thus the huge collection of data becomes complex in terms of data access control and authentication in the distributed environment. Especially, the data access control is not fine-grained, and this may result in data leakage and other security threats. So apart from the traditional security, there is a special focus required in the field of data access control in cloud computing platforms.
See also: Tips for developing secure and flexible management policySee also: Security and Privacy Issues over the Cloud Environment
Brief note of Cloud access control system
Generally, the term data access control system defines the huge collection of components and techniques which define the appropriate administrator to activate valid user on the basis of privileges outlined and preconfigured access permissions in the access security policy. The primary aim of any access control system is restricting a user to exactly what they should be able to do and how can protect data from unauthorized access. There is a wide variety of models, administrative capabilities, methods and technologies are utilized toward design and propose access control systems. Each access control system has its methods and functions, own attributes, that derive from either set of policies or policy. The systematic representation of cloud access control with a service provider is shown in Figure 1.
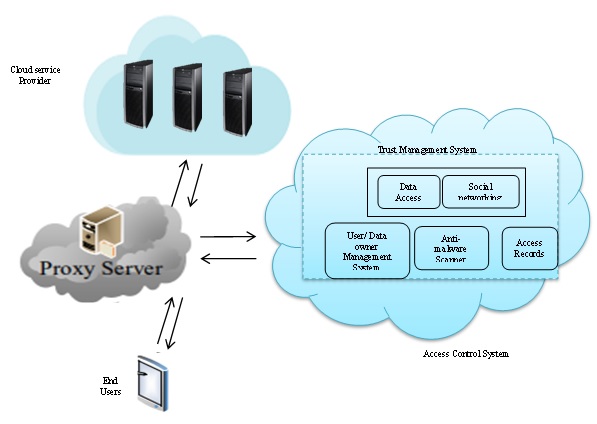
Figure 1: Cloud access control system
Apart from this, one of the primary issues which we are facing is accuracy while we access the data in terms of detecting user behavior. For addressing this issue, there is a potential extension by considering multi-authority access control which aggregates data from different resources to profile the user’s behavior. Developing a novel algorithm using a machine learning approach to classify user’s behavior is significant to bridge the gap among theory and real-time application. The novel algorithm should consider the below factors in order to develop a secure access control system:
- Should consider different flexible functionalities like self-managed and self-defined access control, user-friendly deletion and addition of group users, separation of access authentication from system authentication and iterative access control proxy server.
- Reduce the computational complexity which comprises both encryption and decryption algorithms.
- Multi-authority Access Control and Fine-Grained Data Access Control scheme for supporting dynamic behaviors of users over the cloud platform.
- To enhance the complexity by fast decryption technique and outsourcing the pairing computations to the cloud by adding dynamic attributes.
Summary
The access control and security management framework along with effective machine learning would provide guidance information for the cloud customers and administrators to make decisions, for instance, migrating tasks from dynamically allocating resources, suspect nodes to trustworthy nodes and managing the trade-off among the cost of resources and degree of redundancy.


