Computer Science & IT
Coding & Algorithms Development
- Shrewd Object Visualization Mechanism
- Robotic Process Automation
- Role of AI in Healthcare
- Natural Language Processing
- Edge Computing
- AI For Cybersecurity and Knowledge Breach
- Reinforcement Learning
- Machine Learning in Hyperautomation
- The Intersection of ML and IoT
- Consistent Integration with Other Languages
AI For Cybersecurity and Knowledge Breach
AI and machine learning (ML) have become critical technologies in information security, as they are able to quickly analyze millions of events and identify many different types of threats – from malware exploiting zero-day vulnerabilities to identifying risky behavior that might lead to a phishing attack or download of malicious code. These technologies learn over time, drawing from the past to identify new types of attacks now. Histories of behavior build profiles on users, assets, and networks, allowing AI to detect and respond to deviations from established norms.
Unfortunately, AI is a very popular, often misused buzzword at the moment. Not unlike big data, the cloud, IoT, and every other “next big thing”, an increasing number of companies are looking for ways to jump on the AI bandwagon. But many of today’s AI offerings don’t actually meet the AI test. While they use technologies that analyze data and let results drive certain outcomes, that’s not AI; pure AI is about reproducing cognitive abilities to automate tasks.
Hope you Enjoy information till,Looking to hire thesis writing expertise for the Artificial Intelligence For Cybersecurity Can whatsapp us +91-8754446690
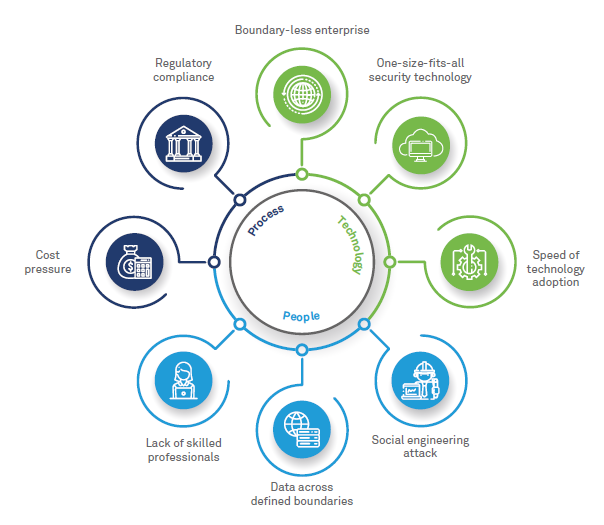
Fig.1. Eliminating the complexity in cybersecurity with AI (Wipro.com)
In recent years, AI has emerged as a required technology for augmenting the efforts of human information security teams. Since humans can no longer scale to adequately protect the dynamic enterprise attack surface, AI provides much needed analysis and threat identification that can be acted upon by cybersecurity professionals to reduce breach risk and improve security posture. In security, AI can identify and prioritize risk, instantly spot any malware on a network, guide incident response, and detect intrusions before they start. AI allows cybersecurity teams to form powerful human-machine partnerships that push the boundaries of our knowledge, enrich our lives, and drive cybersecurity in a way that seems greater than the sum of its parts.
